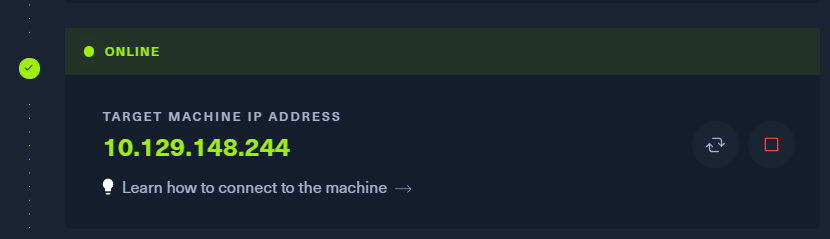
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
| ┌──(kali㉿kali)-[~]
└─$ rustscan --top -a 10.129.150.160 -b 1000 -t 5000 -u 5000 -- -A -sV 1 ⚙
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.129.150.160:3306
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-29 06:57 EDT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 06:57
Completed NSE at 06:57, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 06:57
Completed NSE at 06:57, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 06:57
Completed NSE at 06:57, 0.00s elapsed
Initiating Ping Scan at 06:57
Scanning 10.129.150.160 [2 ports]
Completed Ping Scan at 06:57, 0.97s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 06:57
Completed Parallel DNS resolution of 1 host. at 06:57, 1.03s elapsed
DNS resolution of 1 IPs took 1.03s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 06:57
Scanning 10.129.150.160 [1 port]
Discovered open port 3306/tcp on 10.129.150.160
Completed Connect Scan at 06:57, 0.24s elapsed (1 total ports)
Initiating Service scan at 06:57
Scanning 1 service on 10.129.150.160
Stats: 0:00:56 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 0.00% done
Completed Service scan at 07:00, 173.98s elapsed (1 service on 1 host)
NSE: Script scanning 10.129.150.160.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:00
NSE Timing: About 99.30% done; ETC: 07:00 (0:00:00 remaining)
Completed NSE at 07:01, 44.50s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:01
NSE Timing: About 87.50% done; ETC: 07:01 (0:00:04 remaining)
Completed NSE at 07:01, 44.25s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:01
Completed NSE at 07:01, 0.00s elapsed
Nmap scan report for 10.129.150.160
Host is up, received conn-refused (0.88s latency).
Scanned at 2021-10-29 06:57:31 EDT for 265s
PORT STATE SERVICE REASON VERSION
3306/tcp open mysql? syn-ack
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.27-MariaDB-0+deb10u1
| Thread ID: 82
| Capabilities flags: 63486
| Some Capabilities: Support41Auth, Speaks41ProtocolOld, ODBCClient, ConnectWithDatabase, InteractiveClient, DontAllowDatabaseTableColumn, IgnoreSigpipes, SupportsLoadDataLocal, SupportsCompression, SupportsTransactions, Speaks41ProtocolNew, FoundRows, IgnoreSpaceBeforeParenthesis, LongColumnFlag, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: A)Ir%](M*)1XG;3,%p)y
|_ Auth Plugin Name: mysql_native_password
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:01
Completed NSE at 07:01, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:01
Completed NSE at 07:01, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:01
Completed NSE at 07:01, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 265.94 seconds
┌──(kali㉿kali)-[~]
└─$
|